The invention of the personal computer and the advent of the internet came with many benefits. Still, at the same time, these modern marvels also made it easy for ill-doers to carry out illegitimate actions with ease. One such illicit action that is powered by the internet and modern computer technology is carrying out cyber attacks. There are many ways a hacker or a hacking group can carry out a cyberattack on a target. One such method is through Remote Access Trojan injections.
What is Remote Access Trojan (RAT)?
A Remote Access Trojan is a category of malware that opens up a digital backdoor for cybercriminals to gain administrative access over the targeted system, which could be a personal computer or a server. This backdoor into the victim’s device can allow attackers easy access to monitor the user’s overall behavior, system changes, file access, settings updates, network resource access, etc.
Malware developers mainly use a Remote Access Trojan to get full access and to remotely control targetted systems with complete control, including mouse and keyboard. It allows attackers complete control of a desktop or mobile device so that they can silently browse applications and files and bypass common security such as firewalls, intrusion detection systems, and authentication controls.
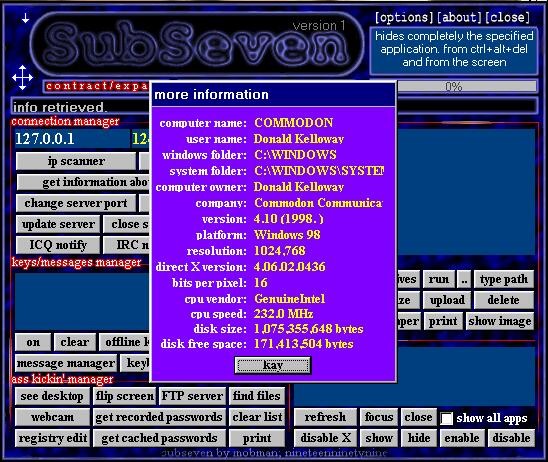
How does it work?
RAT is programmed to embed itself within the setup file of another program that is often requested (downloaded) by an unsuspecting user. For example, remote Access Trojans can be embedded with the setup files of cracked (reverse engineered) computer games or cracked versions of premium software.
They can also be embedded within the source code of an email sent to a target’s inbox. Remote Access Trojan can also be embedded with the attachments usually sent between people working within a company such as a software development brand.
The sole purpose of a Remote Access Trojan is to establish a botnet and offer administrative control over the system, server, or IT infrastructure.
Remote Access Trojan allows cybercriminals to conduct a myriad of illicit activities using an infected system or IT infrastructure, and they could be, but not limited to the following –
- RATs enable cybercriminals to monitor user behavior by installing keyloggers – a type of malware that records the user’s keystrokes using the infected system.
- RATs allow cybercriminals to gain access to sensitive information and then go ahead to steal, alter, encrypt or delete the file.
- RATs can also allow a cybercriminal to activate the webcam and microphone of the infected device so that the user can be recorded without their consent.
Examples of Remote Access Trojan
The best-known example of a Remote Access Trojan is the ‘Back Orifice rootkit’. It was a Remote Access Trojan that was created by a cybercriminal group with the name Cult of the Dead Cow. The purpose of this Remote Access Trojan was to expose the security inefficiencies of Microsoft Corporations’ Windows Operating Systems.
How an Indian hacking group gets infected with Remote Access Trojan
Patchwork is the name of an Indian cybercriminal group that has been on the radar of global and Indian cybersecurity experts since 2015. The group has been associated with several high-profile cyberattacks that include data thefts and related malicious activities carried out on renowned organizations.
Recently the name of the cybercriminal group again popped up on the radar of cybersecurity experts as the group itself became the victim of a Remote Access Trojan attack. It was the latest version of malware created by Patchwork. However, experts learned that the group accidentally infected its IT infrastructure when testing the recently developed malware.
The incident took place on January 7 this year.
Also Read: Why Immutable Data Storage is an Integral Part of a CISO’s IT Security Strategy
It is easy to see from this case study that cybercriminal organizations need to improve their cybersecurity measures as malware(s) do not discriminate! Cybersecurity is the need of the hour. Whether you run a business or spend a considerable amount of time online, you would need to invest in cybersecurity measures by consulting with a cybersecurity service provider today for the best results.
To protect your devices and systems from such dangerous Remote Access Trojan, one should always perform the best cyber security practices.
- Always use antivirus software and ensure that it runs the latest version.
- You need to check that the antivirus software’s virus definition in your system is the latest one.
- You need to refrain from accessing sites that offer cracked software and applications.
- You need to be vigilant while opening email attachments.
- You need to refrain from attaching USB drives to your personal or office computers that came from people you don’t know.
- If your system generates a lot of outgoing traffic using the internet at your home or office, it could be infected. Consult with an IT security consultant as soon as possible for the best results.