Statista says that 71% of global businesses felt the impact of ransomware trends. A total of 62.9% of the ransomware victims paid the ransom. In 2022, CERT-In (Indian Computer Emergency Response Team) revealed a significant surge of 53% in ransomware incidents within India. Alongside this rise, new strains like Vice Society and BlueSky emerged, and tactics like double and triple extortion were used. Hackers used myriad techniques and tools to infiltrate networks, applications, and computers as they lay the groundwork for the ransom demand. This is why a Secure Access Service Edge (SASE) solution that focuses on protecting these assets against ransomware is your first line of defense against attackers.
Increased Risk with Flexible Work
Ransomware can exploit access to corporate resources, including data centers, IaaS, and cloud production environments, to propagate within your organization, blocking you from vital IT assets. The danger of infection and spread is multiplies when users operate beyond the corporate firewall. Remote employees might unknowingly download a contaminated file, interact with a malicious advertisement, or visit an infected website.
Moving Targets in Cost, Conduct, and Code
According to CSO Online, in 2022, 76% of organizations were targeted by a ransomware attack, out of which 64% were infected with only 50% able to retrieve their data after paying the ransom. IBM’s Cost of a Data Breach 2022 report revealed an average ransom payment of $812,360, with the total cost of a ransomware attack standing at $4.5 million on average.
As costs to victimized organizations increase, so do the number of ways in which attackers carry out their attacks. Individuals conducted the first ransomware attacks, developing and distributing massive numbers of automated payloads to randomly selected victims. Today, attackers are sophisticated, operating full-blown “business models” like ransomware-as-a-service with careful planning and execution tactics.
Once inside the network via malware and/or system vulnerabilities, some attackers encrypt sensitive data and threaten to expose it. Decryption keys might—or might not be—released after the ransom is paid. Some ransomware attackers skip the encryption phase and simply threaten the victim showing copies of stolen data. “Triple extortion” threats threaten the organization and employees, business partners and clients. Still other attackers simply destroy data.
Ransomware code itself has evolved. The notorious Wannacry combined exploit code stolen from the U.S. government with custom code to create a ransomware worm, which could spread in a network instead of simply encrypting a single workstation. In May 2017, a global Wannacry attack infected an estimated 200,000 computers within three days, costing global victims billions of dollars. Since 2020, VirusTotal’s Ransomware in a Global Context report found more than 130 different ransomware strains, with 95% of them Windows-based executable files or dynamic link libraries. Last year, Check Point Research also observed ransomware gangs using legitimate IT software, such as remote management solutions, in their attacks.
A Real Life Scenario – Preventing Ransomware with SASE
An example of SASE with real-time, global threat intelligence preventing a ransomware attack occurred in a Check Point customer’s environment.
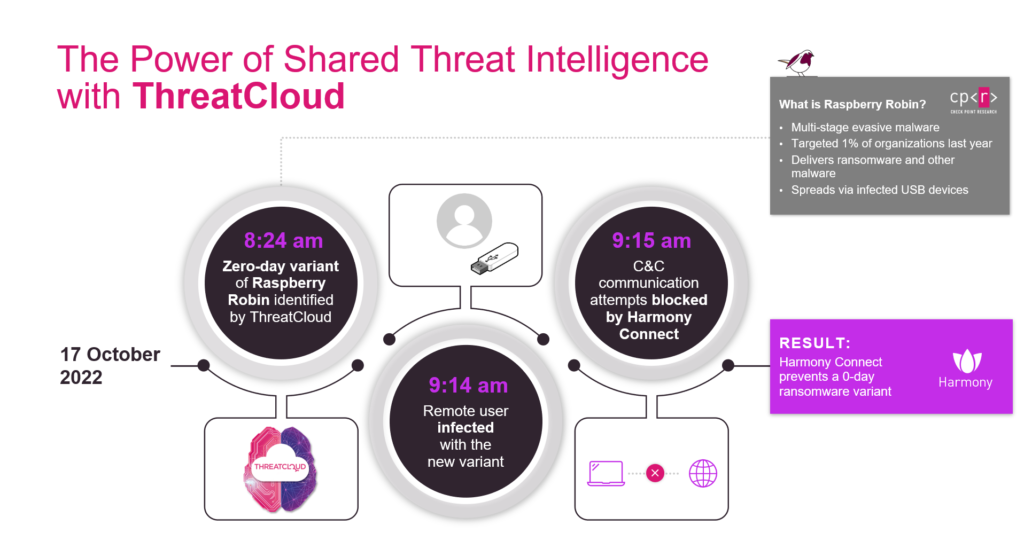
Figure 1: How Check Point’s SASE solution prevented a ransomware attack.
In October, 2022, a zero-day variant of a multistage evasive malware known as Raspberry Robin was identified by ThreatCloud. About 45 minutes after the variant was added to ThreatCloud, a remote user was infected by the variant from a USB device. In less than a minute, the customer’s Check Point SASE solution stopped command & control communications from the malware—neutralizing the attack, preventing the malware from being activated, and avoiding its spread in the customer’s network.
Layered Defense with SASE and Endpoint Protection
A SASE solution, such as Check Point Harmony Connect, serves as a first line of defense against known and unknown zero-day ransomware attacks by securing corporate access and internet access for remote users and branch offices. Harmony Connect prevents the exploitation of vulnerabilities across browsers, applications and systems to stop ransomware from gaining a foothold in your network, while preventing users from accessing infection points and downloading malicious files through real time threat intelligence and advanced sandboxing.
Deploying additional endpoint security, such as Check Point Harmony Endpoint with Anti-Ransomware features, provides a last line of defense against the most sophisticated ransomware, preventing it from encrypting files on devices.
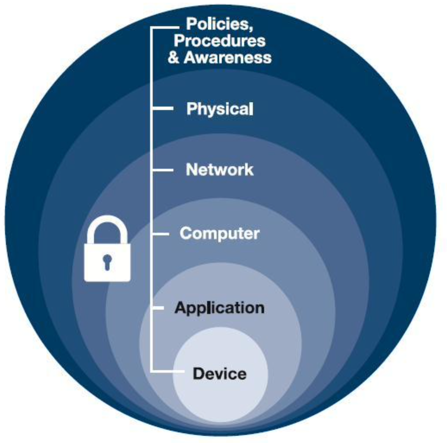
Figure 1: SASE provides layered protection at the application, computer, and network level.























