The fog has lifted to reveal photos of cities around the world with clearer skies – an unexpected silver lining in this pandemic. The next time you look skyward, may I suggest that you take a closer look at the clouds dotting the sky too? We often miss not only the beauty of the atmosphere’s omnipresent cloud but also cloud interfaces integrated all around our homes, offices, and public spaces.
Amid the COVID-19 pandemic, many countries across the world opted to go under a ‘lockdown’ to ‘flatten the curve’ of infection. These lockdowns meant confining the citizens to their homes and shutting down businesses. While it has definitely slowed down economic activity, certain kinds of businesses have experienced tremendous growth. Take Netflix, for example. Owing to social distancing and stay-at-home orders, it is but obvious that people are keeping themselves entertained through multimedia streaming apps. For the first quarter of 2020, new Netflix subscriptions reached 15.8 million surpassing the earlier prediction of 8.8 million.
This brings us to the question of how Netflix could cope with such a massive surge in usage. The answer is the public cloud. Apart from the almost instant scalability it brings, the cloud-based business model used by companies such as Netflix allows them to not just scale when required, but also handle shifts in traffic patterns—all the while remaining reliable to their customers.
It is clear that the pandemic will accelerate cloud adoption. The opting for a cloud environment, once viewed as an option, will now witness greater urgency, due to the many benefits it brings. According to the annual State of the Cloud Survey, 30% of large enterprises expect their cloud usage to increase as a result of the present crisis significantly. Furthermore, among SMBs and enterprises, a net 47% of organizations plan for increased cloud usage because of the changes that the pandemic has brought on. However, this increasing reliance on the public cloud comes with several underlying challenges, the biggest of which is misconfigurations.
Misconfigurations—the biggest challenge in cloud environments
It is vital to remember that moving to the cloud does not mean all risks are eliminated. While some risk factors are reduced, others are introduced. Cloud environments face security vulnerabilities on several counts, from the failure to maintain proper security hygiene to system vulnerabilities at the end-user level. In fact, according to research conducted by Crowd Research Partners, nine out of ten cybersecurity experts are highly concerned when it comes to cloud security.
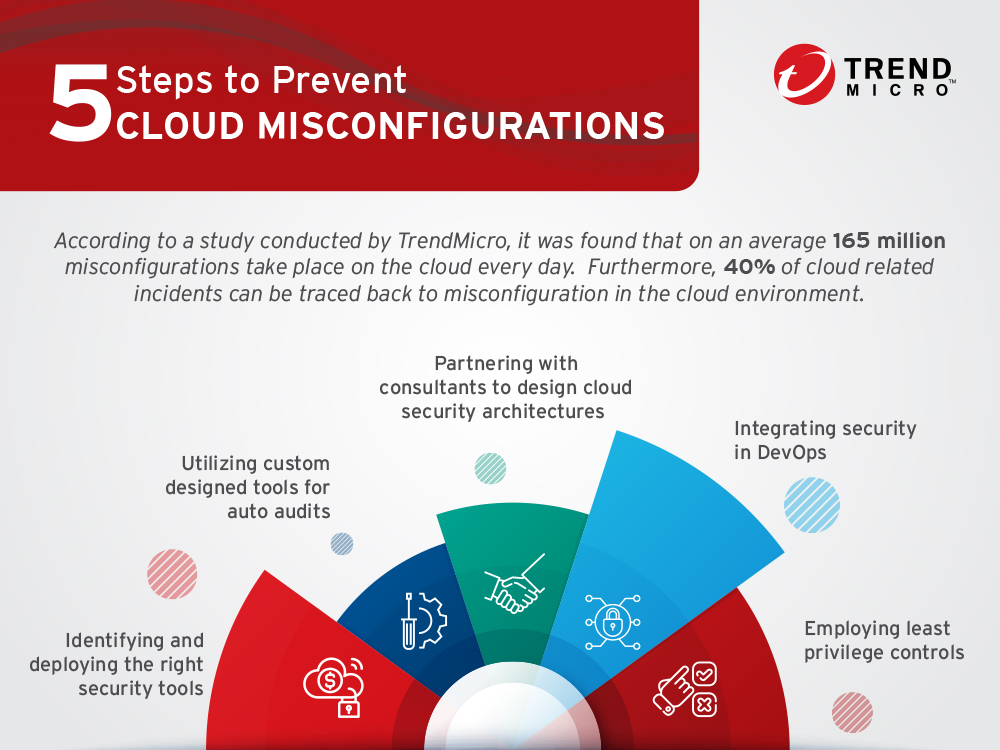
Biggest among these threats are misconfigurations, which to put it in the simplest of terms are the mistakes of the IT teams as they set up the organization’s cloud infrastructure. According to a study conducted by Trend Micro, it was found that on average 165 million misconfigurations take place on the cloud every day. The same study also pointed out that four out of ten— 40%—of cloud-related incidents can be traced back to a misconfiguration in the cloud environment.
It is necessary to understand why misconfiguration is such a big threat. Let’s take an example we are all familiar with—an iPhone. Before starting to use a new phone, the security settings on the phone needs to be configured, to be changed from the default setting. Setting up privacy measures such as passcodes, fingerprint analysis, whether one wants to upload a picture of oneself to their Apple account, etc., has to be set up. Similarly, when an organization migrates their workloads to a cloud platform, security needs to be configured. Nevertheless, inadvertent misconfigurations are common. For instance, an application team configuring a workload whose prime concern would be application connectivity may unintentionally misconfigure the connectivity, thereby overlooking network security.
Another reason for the rise in cloud misconfigurations can be attributed to the lack of visibility and rapid public cloud adoption. Without adequate visibility, security teams are unable to secure cloud environments. Furthermore, as the percentage of adoption grows, the volume of activity proportionally increases, leading to additional misconfigurations such as a lack of awareness of cloud security and policies, the lapse in supervision, lack of or insufficient control, and negligent internal activities. Add to this the number of services being provided by public cloud providers and it is easy to understand why misconfigurations occur. AWS, for example, between the years 2007 and 2017, has added 100 services to its portfolio, which roughly works out to around 10 services each year. This number spiked in the last two years alone, with their portfolio of services adding over 75 offerings.
On top of configuration visibility issues, container which has emerged as a solution for complicated micro service based cloud native applications (through the flexibility it provides) causes security teams to have very less visibility. This can be primarily attributed to the shared responsibility shift in DevOps, which then results in forgotten systems and undeleted logs which can turn out to be a hidden vulnerability.
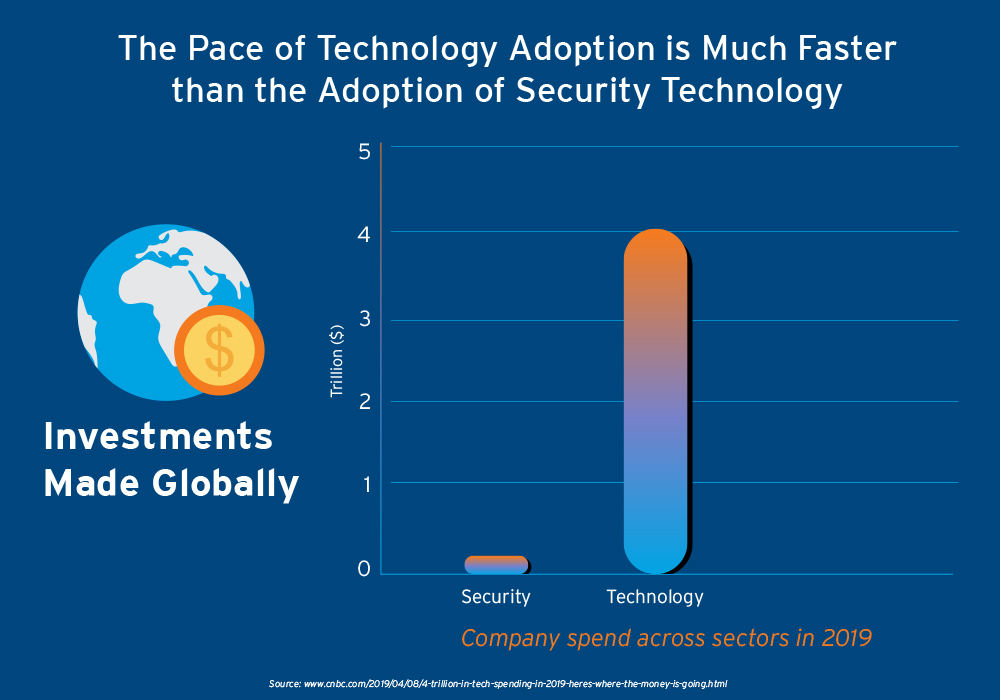
Underlying all these challenges is the fact that the pace of technology adoption is much faster than the adoption of security technology. For instance, by the time an enterprise adopts the use of containers, serverless technology emerges as another level of abstraction on top of containers—making it all the more difficult for security teams to keep up.
Steps to avoid misconfiguration
The number of security breaches steadily increasing due to misconfiguration makes it all the more important for enterprises to take the right steps to prevent these. The need of the hour is for security teams to deploy a single security tool that offers the equal amount of visibility and security for both on-premise applications and new generation container and serverless based micro services applications. The next best practice would be for organizations to deploy custom design tools which can perform an auto-audit of any misconfiguration, thereby matching the best practices guidelines offered by vendors and provide solutions on the go. Finally, it’s always best to partner with professional security consultants, who can help design security cloud architectures that will match future needs. Additionally, simple measures such as integrating security in DevOps from the very beginning and employing least privilege controls which restricts access to only those who need it will also go a long way in protecting cloud infrastructures.
Enterprises are equally responsible for their assets on the cloud
Most public cloud providers operate with a shared responsibility model. While the onus is on them to protect the infrastructure, it is up to enterprises to be responsible for securing their applications, data, operating systems, access management, and firewalls. Preventing misconfigurations then becomes the vital first step in ensuring security for assets on the cloud.
Disclaimer: The author of this article is Nilesh Jain, Vice President, Southeast Asia, and India at Trend Micro. All views expressed in the post are the author’s and the publication does not claim rights to it

























